Becoming ever more common, phishing attacks are emails that try to lure you into revealing login credentials and passwords, financial information, or other confidential data. By asking you to click a link or a button, phishing emails lead you to websites that encourage you to enter the hackers’ sought-after information. Unfortunately, these messages are slipping through spam filters more nowadays than ever before.
To help you avoid falling prey to phishing tricks, take a look at some example screenshots below. These illustrations come from real phishing emails, and we’ve identified key parts of each message that indicate the email is a scam.
Fake Password Expiration Scam
Our first example is a password expiration scam: the idea is to get you to click a button to keep your ‘password’ from ‘expiring.’ The ironic thing about this scam is that there is actually no reason to change a strong and unique password, unless its associated website suffers a breach.
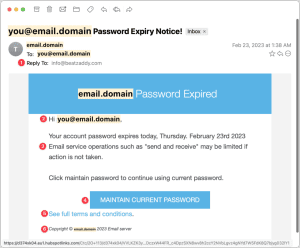
- The Reply-To address is generic, and it also does not match either the “email.domain” used throughout the message or a major email service provider—the latter of which would never send such a message.
- To make the message seem more personalized, scammers use your email address instead of your name. If this message was really sent by your IT department, however, IT personnel would be more likely to use your name, or at least leave out the email address—and they would never send such a message either.
- While the body of the message uses likely words, they don’t quite sound like they were written by a native English speaker. The phrasing and use of quotation marks are slightly off.
- In many email applications, hovering over a button or link will display a URL at the bottom of the window, showing you the website to which you’d be taken if you clicked through to it. Here you can see that the URL differs completely from any other domain listed, which is a clear sign that the email is a phishing message.
- The phrase “See full terms and conditions” is unusual for a password-expiration message. Such language exemplifies a non-native English speaker including random phrases seen elsewhere.
- No organization would claim copyright on a simple support message—and even if it did, it would use its business name, not the words, “Email server.”
Illegitimate Account Access Scam
In our second example, scammers pretend to alert you to a sign-in to your email account, with the goal of scaring you into resetting your password. This phishing email has a good chance of fooling people, because you cannot know if your account has been compromised—and if it were compromised, resetting your password is the right thing to do. However, you should never click through a link from an email in order to change your password; rather, navigate to the site on your own, log in, and then change your password.
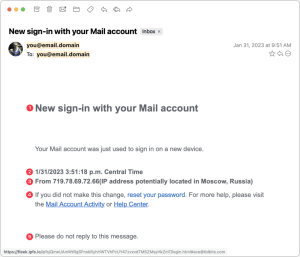
- Most people would not capitalize the word “mail” in the subject line, and instead, they would likely refer to something more specific, such as “Gmail” or “Outlook.”
- The specificity in the timestamp is unusual—there’s no reason to include the seconds or the time zone.
- Savvy Internet users may recognize that real IP addresses are comprised of four sets of numbers from 0 to 255, whereas this IP address has five sets of numbers, with one being out of range (719). Additionally, the missing space before the parenthesis is a red flag, and the mention of Russia is a known scare tactic.
- The link to “reset your password” is not underlined like the other two links, and hovering over it reveals a URL that is not associated with your email account.
- Transactional messages often contain the line, “Please do not reply to this message,” so including it here makes the email seem more genuine. But IT departments sending out real warnings would welcome contact.
Fraudulent DocuSign Confirmation
Our final example masquerades as a DocuSign confirmation of a document that you have already signed. This email merely changes some text of a real DocuSign message, so someone familiar with DocuSign might think it is authentic.
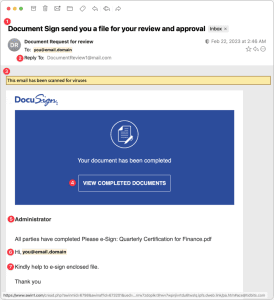
- The grammar in this subject line leaves much to be desired.
- The Reply-To address is far too generic to belong to an organization with which you may be signing documents.
- The yellow line claiming that the email has been scanned for viruses is unusual—and if an email application did present such a message, it likely would not include it in the body of the message.
- Hovering over the “View Completed Documents” button reveals that its associated URL does not belong to docusign.net.
- Individuals familiar with DocuSign messages may notice the missing email address under “Administrator.”
- In lieu of entering your name, scammers commonly attempt personalization by email address.
- Beyond the awkward phrasing, the request to sign the file is mismatched with the blue box that says the document is completed.
Overall Advice
Taking into account the above examples, this distilled advice can be applied to any message:
- Pay close attention to simple emails, as less can go wrong in a straightforward message.
- With messages that appear to be from large firms like PayPal or DocuSign, be aware of unfamiliar names or email addresses.
- It is easy to skim emails and click through them without thinking. Aim to evaluate each message for legitimacy before following any hyperlinks.
- Non-native English speakers often make mistakes in spelling, grammar, and capitalization—read the email’s text carefully.
- When a message makes a claim about something happening within your organization—such as deactivation of accounts or resetting passwords—evaluate the statement against what you know to be true.
- Before clicking, preview the URLs to which buttons lead.
- Emails that only contain an image displayed in the body of the message are fake.
(Featured image by iStock.com/Philip Steury)
